Ain’t No Rest For The Wicked
protection of web applications
Karol Kamiński
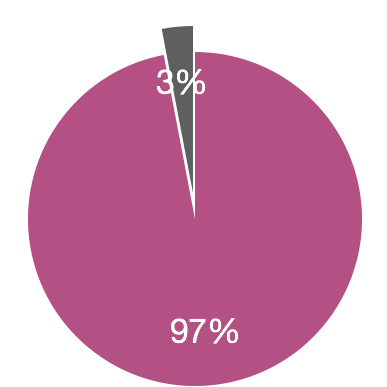
97% of web applications are vulnerable to attacks
Carnegie Mellon University’s CyLab research has shown that 1k lines of code contain an average of 30 bugs.

hint: vulnerability != leak

Mr. Robot: The world is a dangerous place, not because of those who do evil but because of those who look on and do nothing.
OWASP: open web application security project
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Using Components with Known Vulnerabilities
- Insufficient Logging&Monitoring
Sensitive Data Exposure
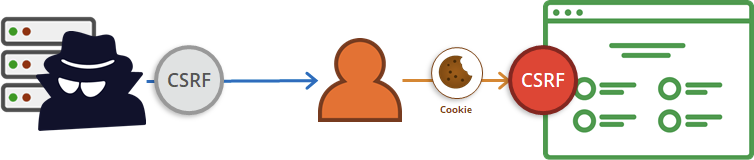
Cross-Site Request Forgery (CSRF)
http://server/admin/users/1?operation=change_pass&new_pass=test123
Cross-Site Request Forgery (CSRF) - remedy
- random token generates on hidden field inside our form before each call to the API (facebook)
- force user to re-log in before crucial actions (allegro)
- check http headers during each request (dangerous)

Cross-Site Scripting (XSS)
Executing some code (especially JavaScript) without any knowledge of the victim
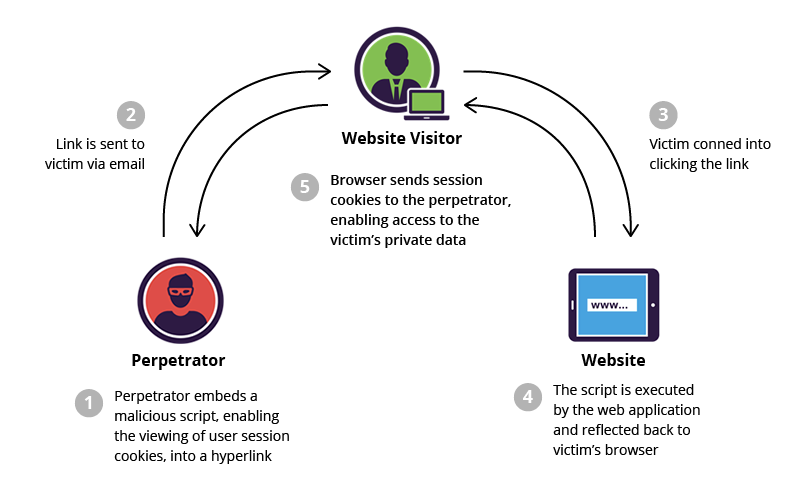
Cross-Site Scripting (XSS) - threats
- steal cookies (especially session ones)
- use the victim as a proxy
- mislead the victim (phishing)
- take control over all system (exploit on a browser)
Cross-Site Scripting (XSS) - types
- Stored XSS - payload stored in a database (e.g. by adding a post or comment)
- Reflected XSS - dynamically executing code (e.g. search fields)
- DOM Based XSS - result of modifications of some DOM element

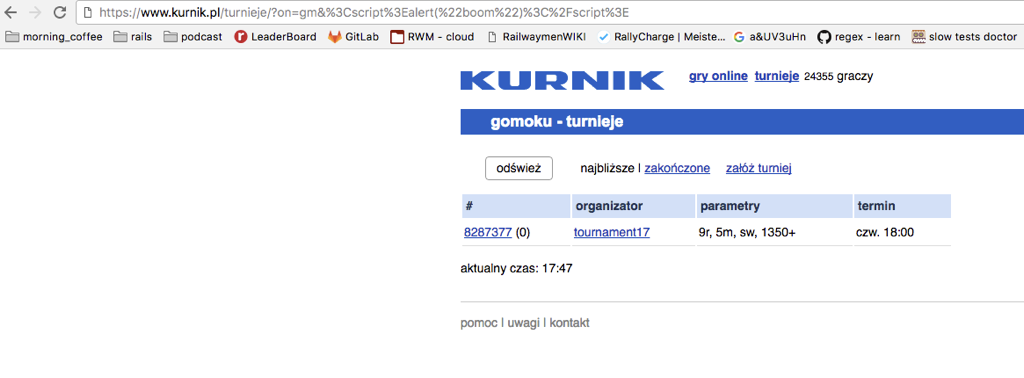
Cross-Site Scripting (XSS) - you tricky bastard!
<script>alert(‘BOOM')</script>
<ʇdıɹɔs/>(,ɯooq‘)ʇɹǝlɐ<ʇdıɹɔs>
[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([] …
%26%238238;%3Cscript%3Ealert(%27BOOM%27)%3C/script%3E

Using web framework makes me bulletproof!
… except … it’s not ;(
Mass assignment exploit
update_attributes(params[:foo])
allowed to make any update on any global variable
TOOLS
- Firefox extensions - XSS Me, HackBar
- Burp Suite - complex tool for pen-testing
- Kali Linux - Linux distribution designed for pen-testing

F. Nietzsche: If you gaze long into an abyss, the abyss also gazes into you.